We’re excited to announce the availability of Role-Based Access Control (RBAC) in StarTree, allowing data users to access different levels of the StarTree platform based on their roles. In this blog, we’ll discuss the benefits of RBAC, how RBAC works in StarTree, and how to configure RBAC using StarTree’s new Security Manager interface.
Why organizations need role-based access
Let’s consider a hypothetical situation where RBAC becomes valuable: Acme Corp has just deployed their StarTree cluster and the team can’t wait to get started with this exciting new technology. However, they also want to make sure that the team members have the appropriate level of access to the StarTree environment and data to do their job well.
Let’s meet the people in the data organization.
Anna the Data Architect
Anna is the architect at Acme Corp. She is responsible for designing the data architecture to meet Acme Corp’s analytical goals. She defines the data standards and policies to ensure consistency, quality, and compliance across the organization. She also evaluates and selects appropriate data technologies to meet the needs of the organization.
Raj the Data Engineer
Raj is responsible for building and maintaining data pipelines and infrastructure. He deploys and manages databases, data warehouses, etc. He also employs ETL techniques to clean and enrich the data. He is also responsible for maintaining and optimizing the performance of the data systems.
Sam the Data/Business Analyst
Sam, the Business Analyst is the consumer of the data and leverages it for a wide range of critical tasks, such as: fraud detection, supply chain optimization, and customer churn prediction.
Claud the System Administrator
Claud is not directly responsible for working with data, but he deploys, manages, and optimizes the compute and storage infrastructure that is critical for running smooth data operations.
Role-based access requirements
Let’s look at what access is needed by each of these personas.
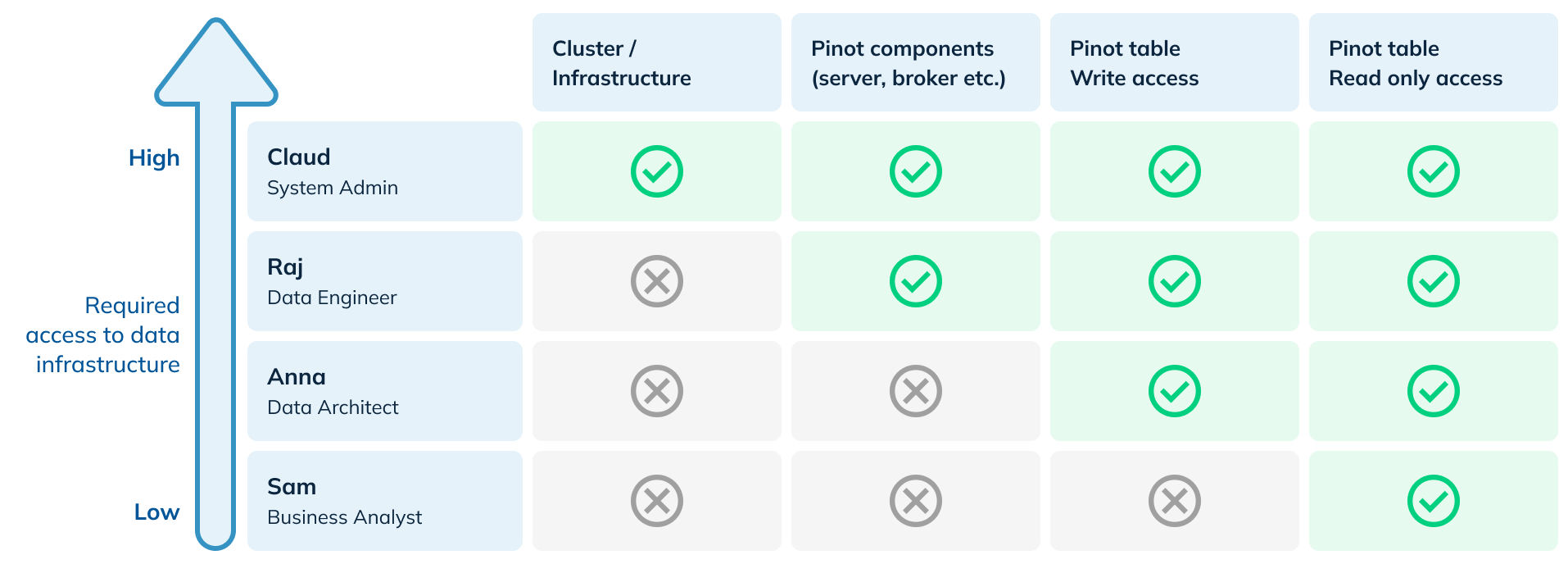
StarTree RBAC Concepts
Role-Based Access Control (RBAC) is an approach to restricting access to authorized users. StarTree Security Manager provides a powerful mechanism to craft policies that match the needs of any data team. Let’s get familiar with these mechanisms.
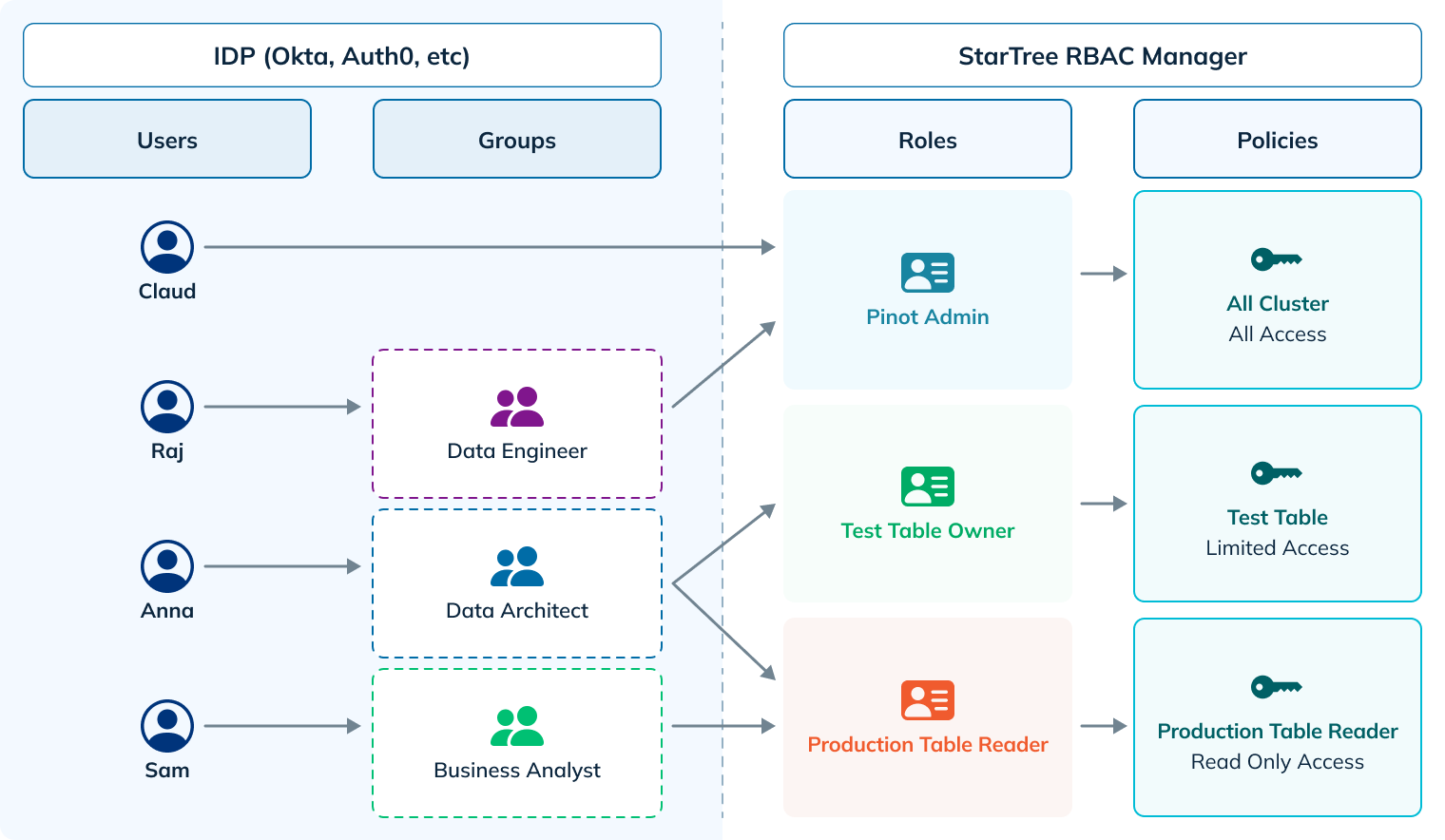
The diagram above shows a typical RBAC system containing users/groups, their roles, and the associated policies. Together, these attributes form the set of rules that define who can access a resource. Let’s take a look at the attributes that are the building blocks for this RBAC system.
Role
A named collection of one or more policies logically grouped together to satisfy an access-control use case. For example, the policy associated with the “Pinot Admin” role allows full access to all of the resources in the Pinot Cluster, while the policy associated with the “Production Table Reader” role only gives read access to the production tables.
Here are some additional examples of different roles that can be created:
| Role | Definition |
|---|---|
Test Table Owner | A role with full permissions for a table named “Test Table”. Users assigned to this role are allowed to change the table configuration. |
Production Table Reader | This role is given read-only permissions to a table named “Production Table”. Users assigned to this role are not allowed to change the table in any way. |
Pinot Admin | This role has admin access to all the tables in the Pinot deployment. Admins can create, delete, and update tables as needed. |
Subject
Roles are assigned to subjects which authenticate into StarTree. A subject can be an individual user (email-id), a user group defined in an IDP, or a service token used for programmatic access.
Policy
A policy is defined as a JSON document that declaratively states which actions are allowed on which resources. A typical policy document will have following structure:
policyDocumentJson : {
statements: [{
description: <>,
resources : [<>],
effect : <>,
actions : [<>]
}],
version : <> }
Code language: HTML, XML (xml)Resource
A resource is any StarTree-managed entity that can be uniquely identified. Resources are identified using a StarTree Resource Name (SRN). SRN is modeled as a hierarchical fully-qualified name for a resource in the StarTree system. Wildcards can be used to identify a resource. Here are some examples of resources:
| StarTree Resource Name | Definition |
|---|---|
cluster#myCluster | Everything in the cluster named myCluster |
cluster#myCluster:table#* | All tables in the cluster named myCluster |
cluster#myCluster:table#Order_* | All tables whose name starts with “Order_” in the cluster named myCluster |
Effect
The effect property dictates whether the policy allows or denies access to the resources identified in the policy. The valid values for the effect property are “allow” or “deny”.
Action
Actions represent the operations that can be performed on a resource. Some examples are:
| Action | Definition |
|---|---|
CreateTenant | Create a Pinot tenant |
CreateTable | Create a new table in Pinot |
Query | Run a query a table in Pinot |
You can find the full list of available actions here.
Putting it all together
Let’s see how we would use these building blocks to define the policies and roles for our personas at Acme Corp.
| Subject | Role | Description | Policy Statements |
|---|---|---|---|
Claud | System Admin | Needs full access to the entire StarTree deployment | Resource: “*” Effect: “allow” Action: “*” |
Raj | Data Engineer | Needs CRUD access to the tables that he is responsible for | Resource: “cluster#*:table#*” |
Anna | Data Architect | Anna needs full access to the tables in her sandbox
However, she should only be granted query access on the production table
Anna should not be allowed to delete any table in any cluster | Resource: “cluster#*:table#Production”
Resource: “cluster#*:table#Test”
Resource: “cluster#*:table#*” |
Sam | Business Analyst | Sam only needs query access for the table that she is interested in | Resource: “cluster#myCluster:table#myTable” |
Configuring RBAC using StarTree’s Security Manager
Now that we’ve figured out our access policies, let’s see how to define them in your StarTree environment. This can be done easily using StarTree’s new Security Manager UI, which is available as part of StarTree’s new Data Portal.
1. First, navigate to the Security Manager at this URL: https://dp.<your_environment_id>.startree.cloud/security-manager.
2. Admins have a built-in system role, so let’s start with assigning the admin role to Claud our administrator
-
- Click on Role assignments
- Click on Assign role
- In the Role dropdown select the system-admin role
- Select user as the Subject type
- Enter Claud’s email in the User email field
- Click Assign role
3. Now let’s create a custom policy for our data engineers
-
- Click on Policies
- Click Create policy
- Enter “FullTableAccess” as the policy name
- Provide a description for the policy
- Enter the following policy configuration JSON
- Click Create policy to save the new policy
{
"version": "v1",
"statements": [
{
"description": "Allow full access to all tables in "myCluster"",
"resources": [
"srn2:cluster#myCluster:table#*"
],
"effect": "allow",
"actions": ["*"]
}
]
}Code language: JSON / JSON with Comments (json)4. With the policy created, the next step is to create the custom role
-
- Click on Roles
- Click on Create role
- Enter “DataEngineerRole” as the role name
- Provide a description for the role
- Check the box next to the FullTableAccess policy from the list of available policies
- Click Create role to save the new role
- 5. Finally, we need to assign the new role to Raj, our data engineer. Simply repeat the process in step #1 above, making sure to select the new DataEngineerRole in the role dropdown
6. You can repeat steps 2-5 to create additional policies, roles and assignments for the rest of our Acme Corp team.
Note: for the data analyst role, you can create a single policy with three statements, or three separate policies (each with a single statement) and group the policies together in a single role. Both options are valid and will achieve the same end result.
Using the API to configure RBAC
In addition to the Security Manager UI, you can also use the API to programmatically create and manage RBAC in StarTree. This allows for seamless integration with existing workflows and automation of security management tasks.
Conclusion
StarTree’s RBAC service provides powerful capabilities to ensure appropriate access to different subjects, so that they are able to do their job without inadvertently mishandling critical business data. StarTree RBAC service is built to deliver high performance suitable for a real-time analytics database, and it is fully compatible with any OIDC-compliant IDP.
Ready to take StarTree Cloud for a spin? Get started immediately in your own fully-managed serverless environment with our Developer Sandbox. If you have specific needs or want to speak with a member of our team, you can book a demo.


